Circle Research releases a @secure_tool extension for OpenAI Agents SDK to automate user approval for AI agent actions and workflows

You don’t want your AI agent to hallucinate and send your crypto to the wrong address because it got two chains mixed up. There must be some way to verify that the transaction the user requests is the transaction that the agent executes.
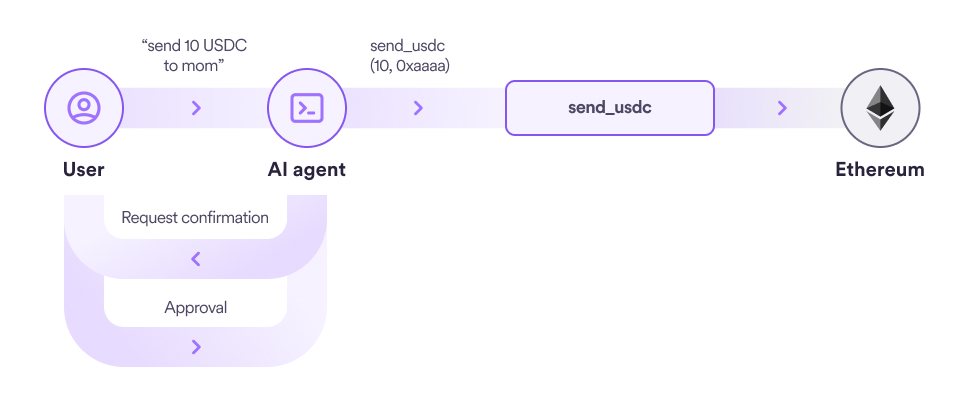
The naive approach is to prompt the LLM to double check with the user. The last thing you want to do with a security sensitive application is to delegate security to clever prompt engineering.
Secure agentic architecture should be built by design, not by prompt. The previous post discussed how to use functions called tools to give agents a safe interface to wallet operations. Agents called the functions to sign blockchain-based transactions but never saw the wallet keys themselves. A LLM that doesn’t know a secret can’t leak the secret. This post shows how to design tools that automatically check whether a particular operation has been approved by the user.
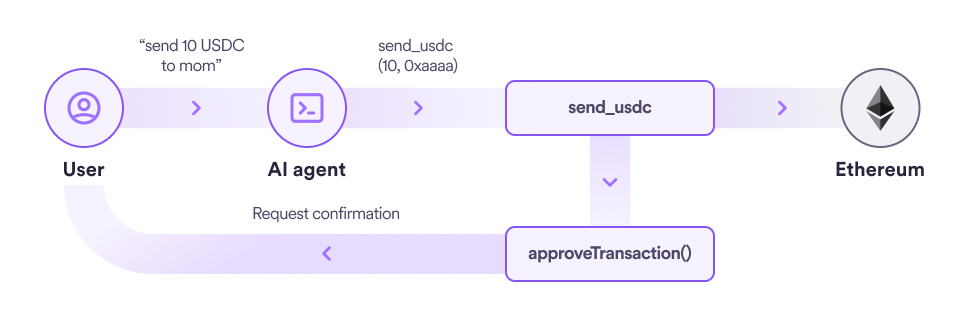
The simplest approach is for the tool to ask the user: is this what you really want to do? Ideally, the AI framework should automate this process so that the developer doesn’t have to add repetitive code.
The previous post introduced OOAK: Object Oriented Agent Kit. This post shows how OOAK lets you build secure agent code that supervises agent actions to ensure it matches user intent.
Introducing @secure_tool
The OOAK framework automates security checking. It introduces a new AI agent tool decorator called @secure_tool that wraps the function call with before-and-after hooks. These hooks connect call-back functions to a class called WorkflowManager. Before executing a function, the @secure_tool will use the before_invoke_tool function to check permission. After executing, the @secure_tool will report the result to the after_invoke_tool.
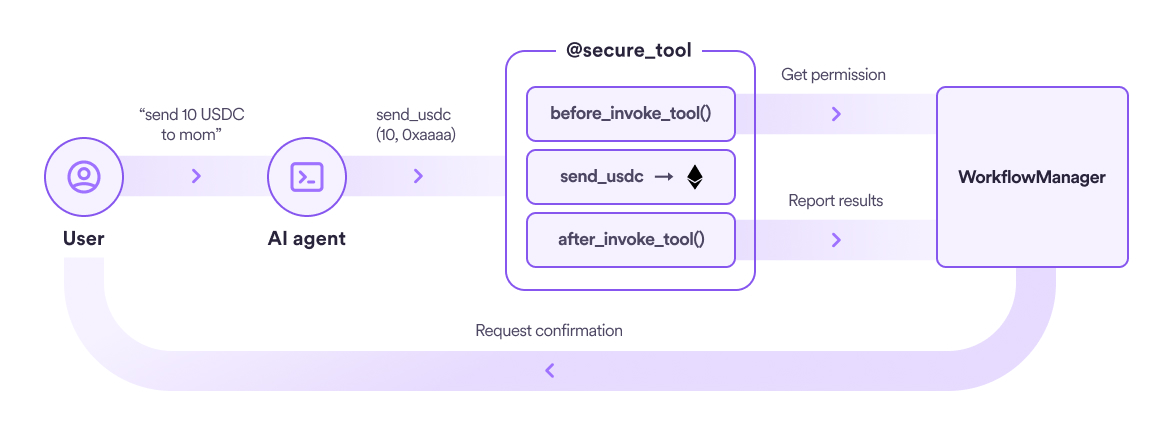
An AI agent action is really just a function name and the list of arguments to that function. In the case of object methods, the action is also specific to the identity of the object instance. Any action, or intent to execute an action, can be represented as a simple json string.
{“instance”: “wallet 3”, "function": "send_usdc", "arguments": {"sender": "0x222222", "receiver": "0xaaaa", "amount": 10}}When the AI agent calls a @secure_tool, the before_invoke_tool function will automatically pass the intent to the WorkflowManager for permission.
Here is how using the @secure_tool and WorkflowManager looks like in practice:
# define a secure tool
@secure_tool
def send_usdc(ctxt: RunContextWrapper[WorkflowManager], wfid: str, sender: str, receiver: str, amount: int):
return wallet.send_usdc(sender, receiver, amount)
# create an agent and give it access to send_usdc
agent = Agent[WorkflowManager](
name="USDC Agent",
instructions="Help the user send USDC using your tools",
tools=[send_usdc],
model=model
)
# run the agent
manager = WorkflowManager()
result = await Runner.run(agent, user_prompt, context=manager)
Actions, Intents, and Workflows
Agentic design is powerful because it lets the AI agent plan a sequence of actions. In the case of blockchain, certain actions need to be executed in a specific order. For example, the user may want to first request USDC via a transferFrom() operation, then check that it succeeded, and only then proceed to send an NFT.
The WorkflowManager class manages a simple linear sequence of intents. The AI agent queries the secure tools with different arguments to build a list of intents. The WorkflowManager exposes a @function_tool approve(intents) that an agent can use to get user approval for the entire workflow in one operation.
After the user approves the workflow, the AI agent can begin to call the secure tools to execute actions. The secure tools notify the workflow manager of each proposed action via the before_invoke_tool and check-off completion using the after_invoke_tool. Each action must complete successfully before the WorkflowManager will permit the next one
Conclusion
The goal of this project is to not only help developers build secure blockchain-based applications, but to also start a conversation about secure agentic design. What does a secure agent architecture look like? How should developers handle permissions, access control, asynchronous tasks, and multi-agent design?
Try the Circle @secure_tool and WorkflowManager.
Note: This article describes technology developed by Circle Research, a division of Circle committed to public good and open-source contributions to push the boundaries of technology used in crypto, blockchain, and Web3. These projects do not represent completed and released software or services. Unless otherwise stated, content published by Circle Research is open-source and is available for anyone to consume, use, and build upon. Due to their experimental and emergent nature, Circle Research innovations are provided to be tested and evaluated at a developer’s or company’s discretion.





